When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
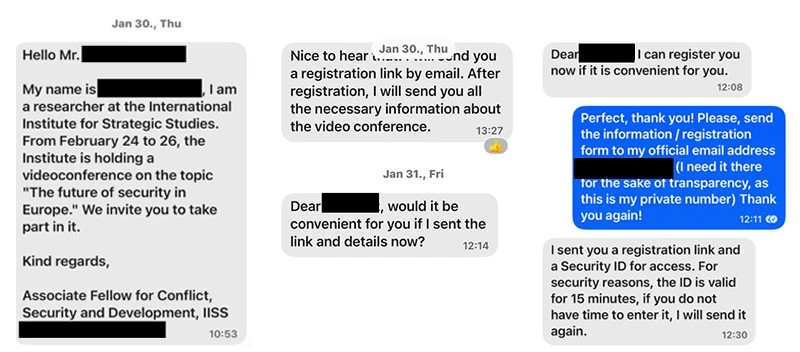
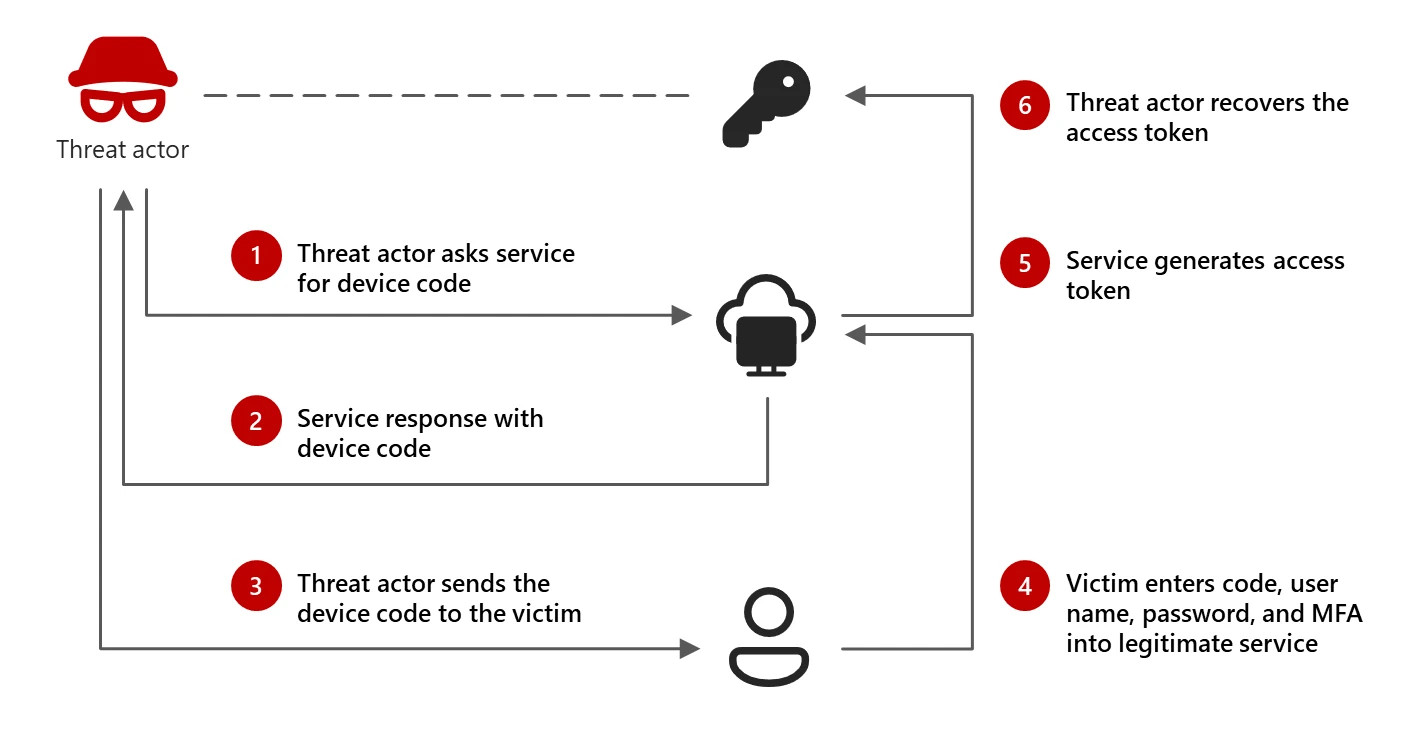
The actor will generate a legitimate equipment code authentication request, and then send the code to the victim.
The attacker can also use the compromised account to message or email colleagues with additional phishing messages.