When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
The victim organizations can be both large enterprises and small- or medium-sized businesses (SMB).
For encryptors, the researchers observed Cring.exe, Ghost.exe, ElysiumO.exe, and Locker.exe.
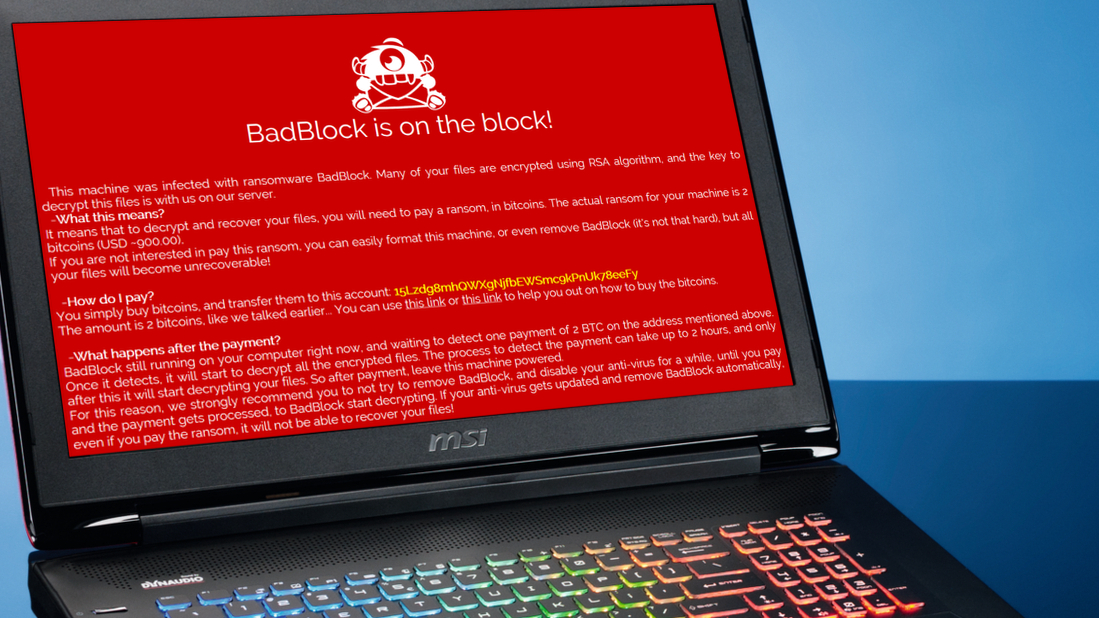
To compromise their victims, the groups went for unpatched endpoints.
The best way to defend against Ghost ransomware operators is to keep your software and hardware up to date.